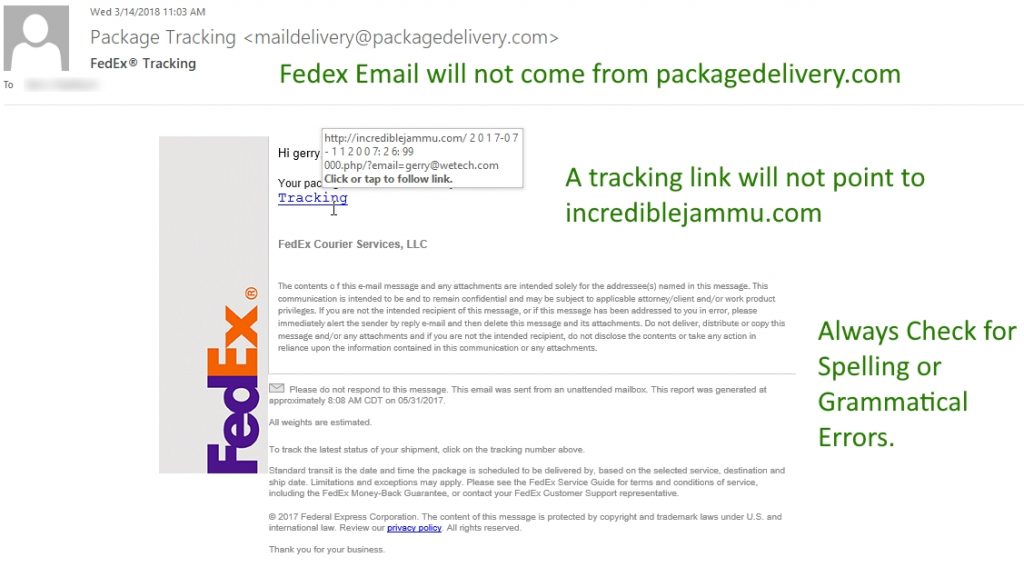
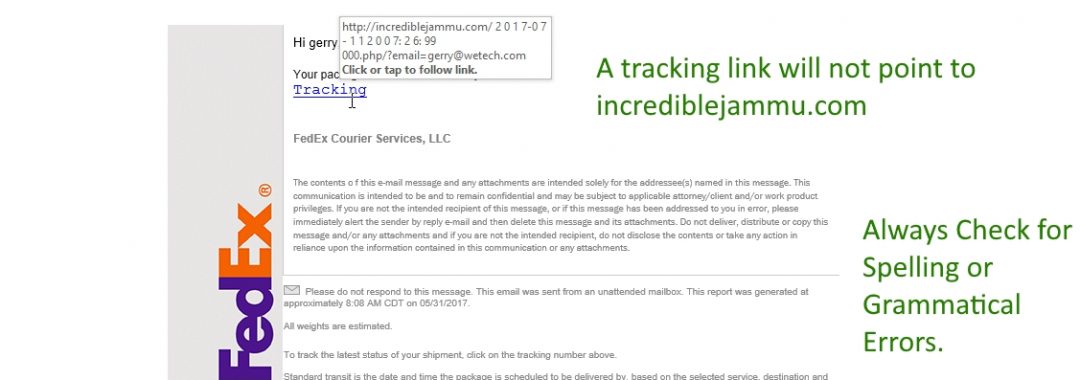
The Problem:
We all have passwords in our lives. How we create them, use them & manage them determines whether or not they will be compromised or in most cases, when they will be compromised and how bad it will be to recover. So lets take steps to be better stewards of our passwords.
You should always create unique passwords that use a combination of words, numbers, symbols and upper and lowercase letters. Most online software will force you to do this anyway. “Th1s!sAG00dPa55word” uses a combination of all these rules.
Longer passwords that use combinations of words are considered a best practice. Most websites will require between 8-12 characters as the minimum in length for a password. The longer the password, the harder it is to brute force attack your way to finding it. It is very easy to find software that will try thousands of passwords to break into your online account. These software packages use dictionaries of common words, combinations of words and or commonly used pass phrases to try. When they get access, they log the username and password they connected with.
Do not use easily guessed passwords such as “password”, “pa55word”, “1234”, “qwerty” etc. These will more than likely already be in a dictionary of passwords to try.
Do not choose passwords based on details in your life that you think may be confidential. Passwords that include your birthday, anniversary, mothers maiden name, family members, pets, phone numbers etc. You would be surprised what you can find online doing a simple google search of a persons name.
Avoid using the same password across multiple websites. If you visit a lot of sites that do not store any personally identifiable information about you, then you could use what security professionals call a disposable password. A password you don’t care gets stolen. For all other websites, that store your real name, phone number, address, etc. you should use a unique password.
Never use a password you’ve already used for an email account. If a website gets hacked and your name and password does get compromised, the first thing a hacker will do is try to get into your email. From there they can get all kinds of identifiable information about you to help them figure out other passwords you may use.
Don’t store a list of passwords on your computer in readable text or with a filename that says it may store passwords. Hackers love to find a file named passwords.txt or websites.txt etc. If you do store passwords on your computer then make sure you store them in a file with a non-obvious name and encrypt the file contents. There are many legitimate software programs that you can use to store usernames and passwords encrypted. Dashlane, LastPass and 1Password store usernames and passwords in the cloud (online) and secure them with a master password and encryption for a monthly cost. Keepass is an example of an open source (free) password storage program that you can use locally that encrypts its contents with a master password.
Web browsers can store passwords to sites you visit frequently. Although this is convenient, most of them store those passwords in readable format if you know where to look. Check the options section of your web browser for a security section and see if there is a way to see your usernames and passwords. If so, see if there is a way to protect them further. Firefox is an example of a browser that stores your usernames and passwords. Make sure you checkbox “use master password” to protect them.
With more and more of our lives being managed online rather than in-person, its all that more important to establish best practices for online security. Password management is a great first step to securing your online presence.